Here is my monthly update covering what I have been doing in the free software world during February 2020 (previous month):
- Attended FOSDEM and CopyleftConf in Brussels, Belgium. Thanks to all the organisers and attendees for making this happen.
-
Further conversations for the next iteration of the OpenUK awards to be presented in June.
-
As part of my duties of being on the board of directors of the Open Source Initiative and Software in the Public Interest (SPI) I attended and prepared for their respective monthly meetings, participated in various licensing and other free software related topics occurring on the internet, had a number of discussions at FOSDEM and CopyleftConf, as well as participated the usual internal discussions regarding logistics, policy, etc.
-
python-debianbts is a Python Interface to Debian's Bug Tracking System by Bastian Venthur. This month I submitted two small pull requests including moving to using the
warnings.warnmethod overlogging.warning[...] and to document missingarchivekeyword argument to theget_bugscall [...]. -
Reviewed and merged two patches for django-enumfield, a library of mine for the Django web application framework to fix tests against some Django versions [...] and to correct an import for migration deconstruction [...].
-
Opened a number of pull requests to make the build reproducible in upstream projects, including:
-
In the
libmate-desktoplibrary component of the MATE Desktop Environment I submitted a pull request to make the build reproducible in/around various dialogs. [...] -
In
python_example, an example pybind11 module built with a Python-based build system, I suggested sorting the extension sources to ensure a reproducible build in any projects based on this template. [...] -
snapd-glib is a GLib library for communicating with the
snapdcomponent of the Snappy package manager. Here, I opened a pull request to make the build reproducible. [...]
-
-
Even more hacking on the Lintian static analysis tool for Debian packages:
-
New features:
-
Bug fixes:
-
Reporting:
- Clarify the error messages when tags are not covered in the testsuite. [...]
-
For the Tails privacy-oriented operating system, I uploaded the following packages to Debian:
-
onionbalance (
0.1.8-5):- Add missing
dh-pythonto Build-Depends. (#952366) - Add
sphinxdoc:Dependsto binary package dependencies. (#832588) - Update Tox dependency for Python 3.x.
- Use
tool:pytestsection in setup.cfg over plain "pytest". - Update build-dependency on
dh-systemdwith debhelper version 9.20160709, specifyRules-Requires-Root: no, use secure URL in debian/copyright, updateVcs-Git&Vcs-Browserand bump the package'sStandards-Versionto 4.5.0.
- Add missing
-
pt-websocket (
0.2-9):
Reproducible builds
One of the original promises of open source software is that distributed peer review and transparency of process results in enhanced end-user security. However, whilst anyone may inspect the source code of free and open source software for malicious flaws, almost all software today is distributed as pre-compiled binaries. This allows nefarious third-parties to compromise systems by injecting malicious code into ostensibly secure software during the various compilation and distribution processes.
The motivation behind the Reproducible Builds effort is to provide the ability to demonstrate these binaries originated from a particular — trusted — source release: if identical results are generated from a given source in all circumstances, reproducible builds provides the means for multiple third-parties to reach a consensus on whether a build was compromised via distributed checksum validation or some other scheme.
The initiative is proud to be a member project of the Software Freedom Conservancy, a not-for-profit 501(c)(3) charity focused on ethical technology and user freedom.
Conservancy acts as a corporate umbrella allowing projects to operate as non-profit initiatives without managing their own corporate structure. If you like the work of the Conservancy or the Reproducible Builds project, please consider becoming an official supporter.
This month, I:
-
Filed upstream pull requests for:
-
In the
libmate-desktoplibrary component of the MATE Desktop Environment I submitted a pull request to make the build reproducible in/around various dialog boxes, etc. [...] -
snapd-glib is a GLib library for communicating with the
snapdcomponent of the Snappy package manager. Here, I opened a pull request to make the build reproducible. [...] -
In
python_example, an examplepybind11module built with a Python-based build system, I suggested sorting the extension sources to ensure a reproducible build in any projects based on this template. [...]
-
-
Attended FOSDEM and CopyleftConf in Brussels, Belgium and had a number of ad hoc meetings regarding the organisation itself, potential future collaborations with other projects as well as to generally represent the project in a wider ense.
-
Begun collaborative work on an academic paper to be published within the next few months.
-
In Debian:
-
Filed a pull request for the core
debian-installerpackage to allow all arguments fromsources.listfiles (such as[check-valid-until=no]) in order that we can test the reproducibility of the installer images on the Reproducible Builds own testing infrastructure. (#13) -
Submitted a patch to
openstack-pkg-toolsto fix a curious issue where packages built differently if they built "too fast" — for example, if we built for both Python 3.7 and Python 3.8 but the installation of the latter occurs within the same wall clock second of the former, the Python 3.8 version will not overwrite the Python 3.7 version and lead to a shebang of#!/usr/bin/python3.7, whilst if it does not occur within the same second, the shebang will be overwritten to#!/usr/bin/python3.8. (#952762) -
I also submitted 9 patches to fix specific reproducibility issues in azure-uamqp-python (nondeterministic
#includedirectives), designate (embedded build path), javatools (nondeterminstic parsing of command-line variables), mate-desktop (build timestamps), msgpack-c (embeds build path), pynwb (embedded timestamps in test files), python-oslo.reports (nondeterminstic/random numbers), snapd-glib (embedded build path) & xavs2 (embedded timestamps).
-
-
Kept isdebianreproducibleyet.com up to date.
-
Categorised a huge number of packages and issues in the Reproducible Builds "notes" repository, including identifying a number of new generalised issues.
-
Authored a report as part of the Open Technology Fund's previous investment in our project.
-
Drafted, published and publicised our monthly report.
-
I spent a few moments on our website this month including improving the documentation for CMake [...], adding a
Meson.buildexample to theSOURCE_DATE_EPOCHdocumentation [...], replacing instances of "anyone can" with "anyone may" [...], correcting/improving the logic to skip commits when generating drafts [...][...][...], etc.
In our tooling, I also made the following changes to diffoscope, our in-depth and content-aware diff utility that can locate and diagnose reproducibility issues, including uploading version 137 to Debian:
- The
sngimage utility will return 1 if there are even minor errors in the file. (#950806) - Also extract
classes2.dex,classes3.dexfrom.apkfiles. (#88) - No need to use
str.formatif we are just returning the string. [...] - Add generalised support for "ignoring" returncodes [...] and move special-casing of returncodes in zip to use
Command.VALID_RETURNCODES. [...]
Debian
I submitted a Request for Package (RFP) bug for hsd, a blockchain-based top-level domain DNS protocol implementation that underpins Handshake and worked on some initial packaging. (#952472)
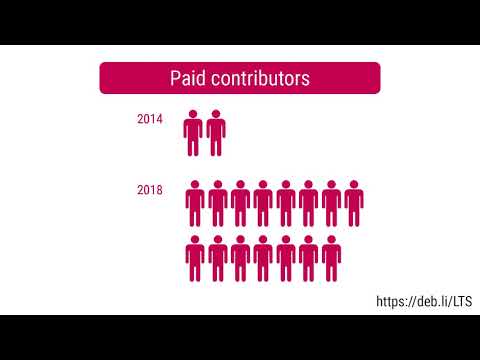
Debian LTS
This month I have worked 18 hours on Debian Long Term Support (LTS) and 12 hours on its sister Extended LTS project.
-
Investigated and triaged:
cacti(CVE-2020-8813),golang-go.crypto(CVE-2020-9283),netty,nodejs(CVE-2019-15605),nova(CVE-2015-9543),ntp,otrs2(CVE-2019-11358)),php-horde-data(CVE-2020-8518),proftpd-dfsg,python-bleach(CVE-2020-6802),python-django,python-pysaml2,qtbase-opensource-src(CVE-2015-9541),ruby-rack,salt,sudo,systemd(CVE-2020-1712),waitress(CVE-2020-5236),wpa(CVE-2019-5061) &yara -
Frontdesk duties, responding to user/developer questions, reviewing others' packages, participating in mailing list discussions, etc.
-
Uploaded version
1.10.7-2+deb9u8to Debian stretch and1.11.28-1~deb10u1for Debian buster to address CVE-2020-7471, a potential SQL injection vulnerability. -
Added DLA 2083-1 in hiredis to the Debian webpages. [...]
-
Issued DLA 2115-1 for the proftpd FTP server to address a use-after-free vulnerability. (CVE-2020-9273)
-
Issued ELA 213-1 for sudo to fix a privilege escalation vulnerability. (CVE-2019-18634)
You can find out more about the project via the following video:
Uploads
-
Django (
2.2.10-1) — New upstream security release. (#950581) -
-
6.0~rc1-2— Add support for Transport Layer Security added in Redis 6.x (#951255) and add a comment regarding why we export aMAKEFLAGSvariable indebian/rules. -
5.0.7-2:
-
-
cpio (
2.13+dfsg-2) — Fix a regression in handling of CVE-2015-1197 with respect to the--no-absolute-filenamesargument by reverting part of an upstream commit. (#946267 #946469) -
hiredis (
0.14.0-6) — Set theBug-Database,Bug-Submit,RepositoryandRepository-Browseupstream metadata fields and rely on pre-initialiseddpkg-architecturevariables indebian/rules. -
1.5.22-1— New upstream release.1.5.22-2— Apply a patch to fix build failures on thes390xarchitecture. (#950777)
-
20.0.4-2— Set the upstream metadata fields (Repository,Repository-Browse, etc.), bumpStandards-Versionto 4.5.0.20.0.4-3— Specify that thegunicornbinary package provides thehttpd-wsgi3virtual package. (#952706)
-
-
4.0.23-2:- Add
future=+lfstoDEB_BUILD_MAINT_OPTIONSto support operating on large files. (#949665) - Add a
gitlab-ci.yml. - Use secure HTTPS URL in debian/copyright, set
Rules-Requires-Root: noand bump theStandards-Versionto 4.5.0.
- Add
-
4.0.23-3— Drop quotes fromDEB_BUILD_MAINT_OPTIONSexport line. (#951037)
-
Finally, I made a non-maintainer upload of adminer (4.7.6-1) on behalf of Alexandre Rossi.